On some of our older SBS 2003 installs where we have no out-of-band remote management setup in place, we open up port 3389 on the router to the server to run our updates.
Once we are finished, we normally close the port back up. Now, this particular evening we had run a series of updates across more than half of the servers that we manage one Saturday.
It seems that one of the firewall ports did not get closed and someone took an interest in that particular server:
- Logon attempts: 3,282
- IP: 64.46.44.76
Now, the IP may not be relevant since the machine behind it may be a zombie.
Things were relatively quite until a few days later:
- Logon attempts: 5
- IP: 113.53.231.2
Then this one kept at it for a number of days:
- Logon attempts: 1,906
- IP: 84.53.64.91
The above IP kept after the server until this day:
- Logon attempts: 2,414
- IP: 84.53.64.91
And another shot of a report that was taken manually in the SBS Console not long after the above:
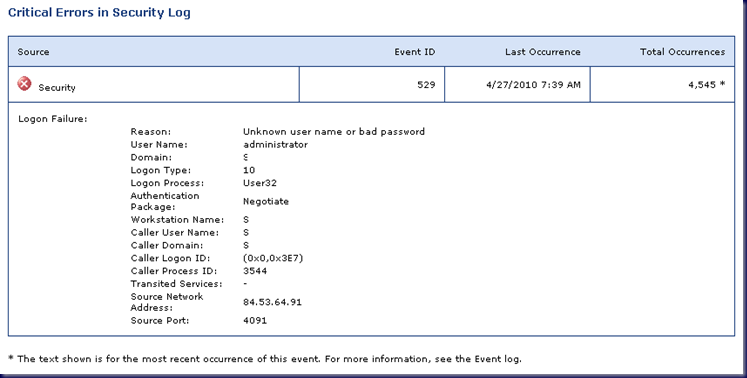
- Logon attempts: 4,545
- IP: 84.53.64.91
Note the different numbers between the automatically generated report and the one manually created by us. The disparity may be due to the fact that the TS service was being hammered so frequently.
While the grind was happening we could not log on to the server via a direct TS connection. We were almost instantly bumped out as soon as we saw the logon screen.
Fortunately, we could log onto RWW and TS via the RWW RDP connection that uses a proxy port of 4125. If that had failed, then we would have connected to a workstation and ran:
- mstsc /v:servername /admin
From there we would have had console access and could do what needed to be done which was to close the 3389 publishing rule in ISA.
TS Client help screenshot:
As a rule, we do not allow port 3389 to be opened to the Internet by default.
Philip Elder
MPECS Inc.
Microsoft Small Business Specialists
Co-Author: SBS 2008 Blueprint Book
*Our original iMac was stolen (previous blog post). We now have a new MacBook Pro courtesy of Vlad Mazek, owner of OWN.





No comments:
Post a Comment
NOTE: All comments are moderated.