Our ailing ISA 2006 standalone server has been a source of pain once we started our migration from SBS 2003 R2 Premium to SBS v7.
We faithfully followed the following sources for setting ISA 2006 SP1 up for SBS 2008:
- Eriq Neale’s ISA Setup Document
- SmallBizServer.net’s ISA with 2006 articles (3 Parts)
- Link is to the ISA 2006 category on the site.
As much as we tried to get things working, we always seemed to run into some really strange roadblocks.
Since we are working with pre-release software, it was tough to troubleshoot problems if there is a third party product, in this case ISA, causing hiccups as well.
For example, the Outlook Address Book would download and update on all Outlook Anywhere connected Outlook clients. None of the internal network clients would update. It turned out that removing the proxy setting in IE, thus bypassing ISA, would allow the OAB to download. The catch though is that e-mail based images and Web content would no longer display within Outlook.
Now, there may very well be a reason for the issues, such as a configuration problem on our part (ID10T or PEBKEC), but after struggling with ISA related issues without discovering a solution for the problem, we threw in the towel on ISA working with SBS v7.
So, we ordered a couple Cisco Small Business Pro SA520-K9 security appliances. One will be for internal use and one is going to a small IT shop that has been sending us some significant collaboration based business over the last six months or so.
Out of the box, the SA520 has an IP address of 192.168.75.1 and its DHCP server service is on.
The default username and password:
- Username: cisco
- Password: cisco
Once we log onto the unit we are greeted with the following “Basic” interface:
Having worked with a number of different vendor’s security appliance/Internet gateway devices, the basic interface as show above is quite refreshing. It is simple and straight forward in its layout and configuration.
Clicking on the Advanced view brings up the following:
Again, a fairly straight forward navigation setup that is easy to follow and easy to use.
Change the Default IP Subnet
One of the first things we do with a new gateway appliance after it is first fired up is to change the internal subnet to the destination network’s subnet _before_ disabling the internal DHCP server service.
This way we can release and renew on the machine physically connected to the security appliance and not have to mess around with static IP settings on the laptop NIC.
After clicking Apply:
Once the appliance rebooted, which did not take very long at all, we released and renewed our IP address on the connected laptop.
When we connected to the SA520 after that we were greeted with:
An Active Session already exists for the User ‘cisco’.
If you want to close the other session, please click on the ‘Continue’ button.
Click ‘Cancel’ button to logout.
SA520 Firmware Update
Once we have the correct subnet set, we then need to check for the most current firmware for the device:
The above link requires a Cisco.com username and password. In our case we used our Cisco Partner ID which gave us access to the software updates folder after clicking through a few path links.
As of this writing, the most current firmware available for the device is:
- Cisco SA520 Series Firmware: 1.1.42
Note that once we clicked through a couple more links to download the software we were presented with a Terms & Conditions page that required a “signature” before the download presented itself.
Then, we were required to accept another agreement, then we needed to click through a few more Download Now buttons to finally get the download moving.
Final Download Page
Ack! There may be a bit of work there to improve access to the firmware download as there had to be at least 20 or more clicks before it even started! :|
There is a feedback page after the download completed, so we made sure to mention that things may be a bit simpler to work with.
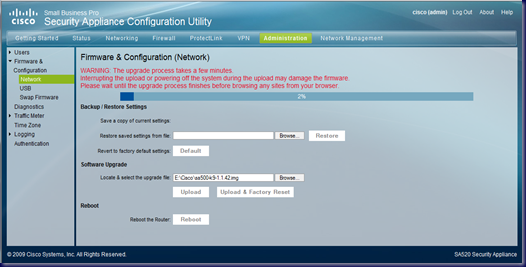
The firmware update process itself is straight forward:
After clicking OK:
Once the upload process completed, we saw a countdown timer:
The Diag LED on the front of the SA520 stayed lit yellow for a good portion of the countdown timer. With about 10 seconds left on the timer the Diag LED went out.
Firmware Update Caveat
Note that since we were updating the firmware on a newly powered up SA520, we did not take the time to save the settings using the Backup/Restore Settings process shown on the firmware update page.
When that countdown timer finished, we were no longer able to get into the SA520.
An IP release/renew showed why:
The settings changes we made for IP subnet and the SA520’s name were gone.
Make sure to backup the settings for the device _before_ running a firmware update or all of the customized inbound and outbound settings _will be lost_!
Note that this caveat is indicated in the firmware release notes to be found via the link below.
Firmware 1.1.42 Release Notes
Recommended Upgrade Steps
When upgrading from version 1.0.15, 1.0.17, or 1.0.39, the firmware will reset the router to its factory default and you will need to back up the configuration. When upgrading from 1.1.21, these steps are not required.
Of course, the firmware release notes were on the way down _after_ the firmware update download since there was no direct link to them on the actual download page. ;)
Once logged in after the update was applied, we checked the firmware page and saw:
We now had the ability to drop our Cisco username and password into the update page so that updates can be downloaded and installed automatically.
For those of us that work in SMB with SBS and other server hardware and software products, this setting is unlikely to be used. ;)
UPnP Status
With most consumer grade gateways, the UPnP feature comes enabled by default.
On the Cisco, we can see that UPnP is disabled by default. Since UPnP is a significant weakness in the overall security of a network, it should be disabled by default.
Conclusion
Now that we have the basics figured out, we are moving on to configuring the SA520 for our multiple ISP provided IP setup that includes a number of different services published to the Internet across those IPs.
We will be ordering in another unit to use as a tester that we can tear apart and work with without breaking our own connections soon!
Philip Elder
MPECS Inc.
Microsoft Small Business Specialists
Co-Author: SBS 2008 Blueprint Book
*Our original iMac was stolen (previous blog post). We now have a new MacBook Pro courtesy of Vlad Mazek, owner of OWN.














We have a pair of SA520's that we are using for a site-to-site VPN, general web access, and remote access. We also have SBS 2008 which provides our internal email, externally it is using the POP3 Connector. My problem is that I have a handful of users that use Outlook Web Access and as soon as I turn on URL filtering on the SA520 my users lose access to OWA! I have tried adding the users to the Approved Clients list and I have tried adding the SBS Server as an Approved URL to no avail. The ONLY category that I have blocked in ProtectLink is Porn. I guess it thinks our email is pornographic. lol
ReplyDeleteAnyway, I was wondering if you might have any suggestions about how to proceed.
Thanks!
Greg