Not only that, the application client on the Windows Vista workstation will most likely need at least a program exception enabled in the Windows Firewall with Advanced Security properties too.
Two settings that need to be enabled after SBS 2008 has been installed and configured to help with troubleshooting:
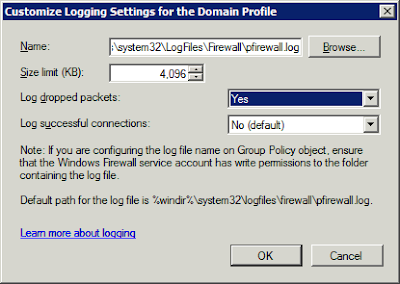
After opening the Windows Firewall with Advanced Security console, right click on Windows Firewall with Advanced Security and click on Properties. Click the Customize button for Logging to enable logging on the domain profile (it should be active).Enable Log dropped packets
And:
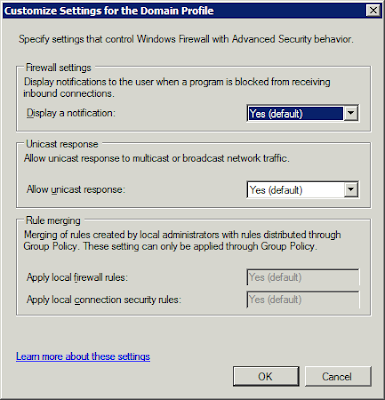
Enable Display a notification
Click on the Customize button for Settings and enable the Display a notification setting so that a pop-up will happen if a newly installed application tries to get out and listen.
With Logging enabled, click on the Monitoring node and a there will be a Hyperlink to the logging file that can be clicked on for quick access. It will indicate any dropped packets, the port they were attempting to connect on, and whether they were UDP or TCP. Client IP is also included along with other details.
Two additional tools for the troubleshooting:
- From the command line: netstat -an >ports.txt [Enter]
- From the command line: PortQry -local >ports.txt [Enter]
PortQry V2 can be downloaded from here: PortQry V2 Download. Both commands will port a list of services listening on what ports using which IP addresses an more.
If the service being troubleshooted shows up in the list as Listening, then the next step is to check that the Vista client is allowing the application client out.
Philip Elder
MPECS Inc.
Microsoft Small Business Specialists
*All Mac on SBS posts are posted on our in-house iMac via the Safari Web browser.
2 comments:
You can also perform these settings changes inside Group Policy.
Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security
tcpview.exe and tcpvcon.exe in the Sysinternals Suite are also useful debug tools.
Chris,
Thanks for the pointers.
Philip
Post a Comment