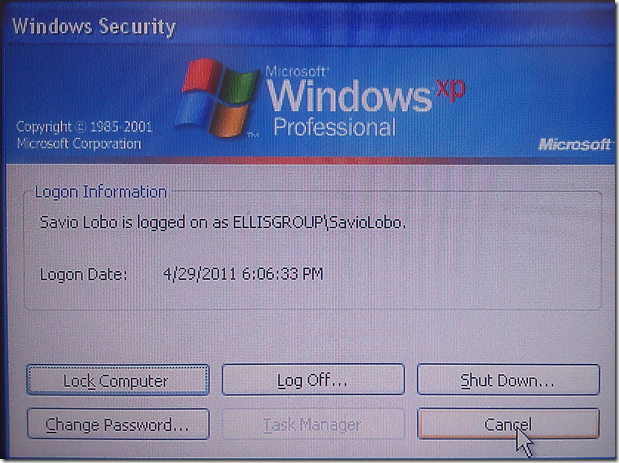
One of our client’s users picked up this lovely nasty:
Note the lack of Task Manager button in the above or below screenshots.
- WindowsRecovery Malware
Now, we went to this site to download Malwarebytes and its updates:
Once we downloaded the two we dropped them onto a USB flash drive and plugged it into the infected machine.
When we managed to navigate to the USB flash drive the MB file was missing?!? We ended up needing to reveal hidden files in Windows Explorer as WindowsRecovery had managed to set the MB install file as hidden!
Okay, we have MB and its update installed. We were able to use the Start –> Run command to get to the mbam.exe file (Windows XP SP3 is where the infection is) but it would not update.
Once we started the MB scan and it began to pick up the infected files the malware rebooted the machine.
When we slaved up the infected machine’s hardware Microsoft Security Essentials picked up one infected file while MB found a few more. We dropped the drive back into the machine and WindowsRecovery was still there. :(
Do a Bing search for Remove WindowsRecovery and the following happens:
If we can’t get the machine clean using the “traditional” product in Malwarebytes then it is looking like the only option for us is to wipe and reload. There is no way we are going to trust many if not all of the sites that are in the results above. Especially all of the ones offering a “free removal tool”.
If this is a sign of the way things are going with malware infections we are going to stop wasting both our client’s time and ours and advise that we would image the machine, wipe it, and then reload it.
Now, here we are a little later on and what do we find but:
After reading through the above instructions, we will still recommend a wipe and reload. Our policy is to make this recommendation whenever a Trojan or Rootkit are involved. Once a system is owned in this manner there is virtually no way to guarantee ownership after “cleaning”.
Philip Elder
MPECS Inc.
Microsoft Small Business Specialists
Co-Author: SBS 2008 Blueprint Book
*Our original iMac was stolen (previous blog post). We now have a new MacBook Pro courtesy of Vlad Mazek, owner of OWN.




7 comments:
I had a customer get this virus the other day. I indeed ended up rebuilding his laptop.
Pete
I have yet to reimage, thanks to SysInternals. It can take longer to get them disinfected but any customer who's experienced a rebuild would be happy to pay the extra for it.
Our strategy to deal with this kind of infection is to first use Windows System Restore to restore the system to a point prior to the infection, then use Malwarebytes' Anti-Malware to check for any infected objects that are left behind. Most of the time this strategy seems to work.
Hi Philip,
The same over here. After some hours of study, I decided to restore the image (ShadowProtect again to the rescue!). What a terrible infection!. Is it stealing creditcard information?
Regards,
Leen Kleijwegt
Netherlands
We've had some users with this and this year's Anti-Virus 2011 virus. We don't try to remove them anymore, reboot into safe mode and do a system restore from there. Then run Malwarebytes and some kind of antivirus scan on top just to make sure. There have been some versions of the Anti-virus 2010 that prevented system restore from working in regular mode. Safe mode seems to be still able to get them (for now)
When it comes to System Restore and stepping things back there are still no guarantees that the system was not rooted.
Stepping back via SR does may not remove a rootkit.
It becomes a risk evaluation exercise that we would run with our client. Those that insist on a "cleaning" must sign a document absolving us of any responsibility for lost data, compromised identity, etc. The decision is _that_ serious.
ShadowProtect at least does a bit by bit restore of the system at the time of the image snapshot. The catch then becomes figuring out which one is good to restore from and whether the data can be trusted from any subsequent SP image.
Philip
I use malwarebytes and then I run Combofix. Combofix will get what Malwarebytes missed and unhide the files.
I'm just sick of my antivirus not being able to stop these kinds of thing for customers.
Post a Comment